Pentesting Weekly Digest - October 4–10, 2025
Apple bounty doubles, ransomware in Japan, and a new Oracle 0-day exploited in the wild.
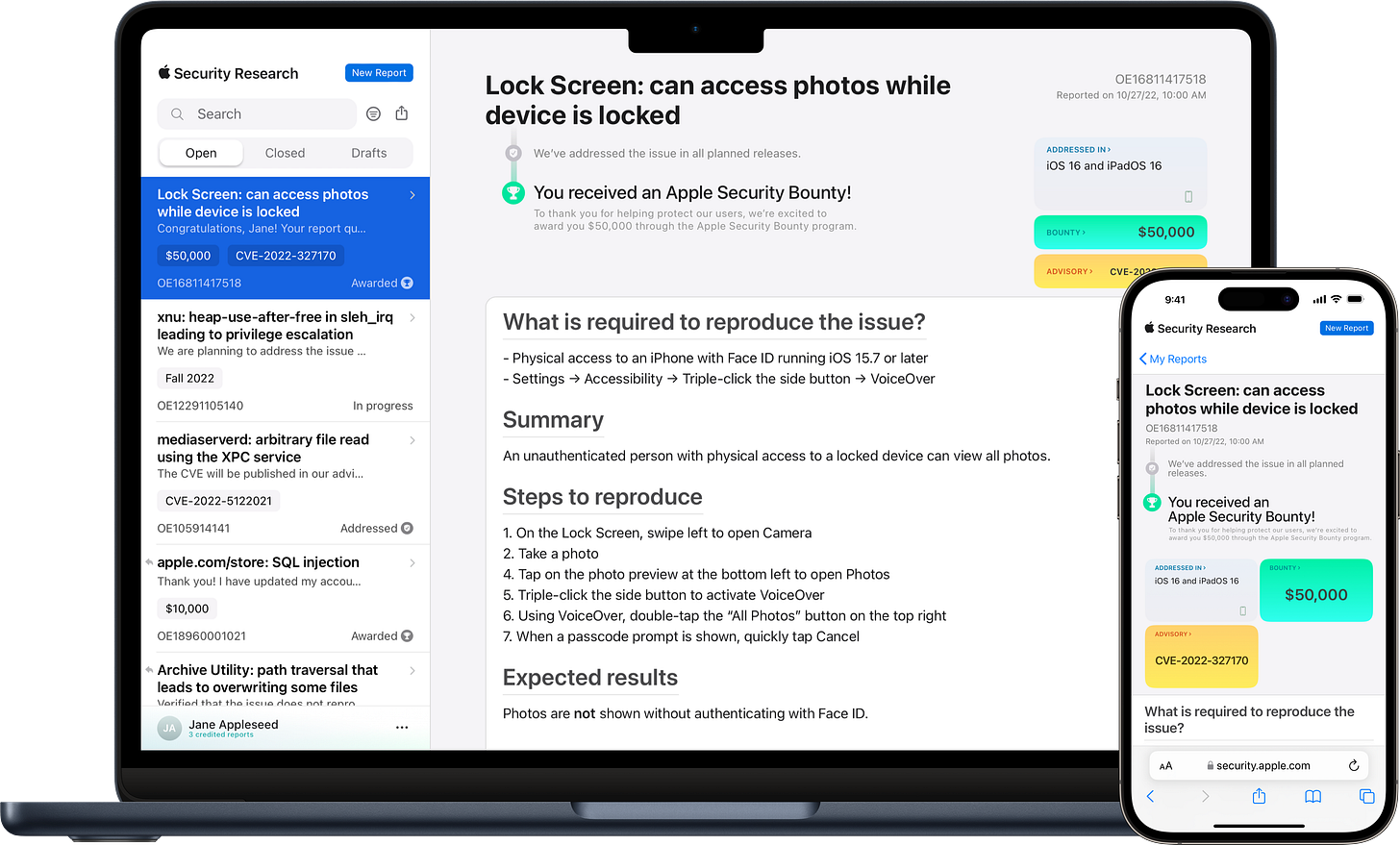
🔹 Apple Security Bounty - up to $2M for zero-click chains
Apple updated its bug bounty program: payouts rise to $2,000,000 for spyware-level zero-click or proximity exploits, plus new Target Flags bonuses for complex chains starting this November.
🔗 Apple: New Security Bounty Program
🔹 Qilin ransomware hits Asahi Group (Japan)
The Qilin gang claimed responsibility for breaching Asahi Group and leaking ~27 GB of internal data. Production has been restored; investigation is ongoing.
🔗 Reuters: Japan’s Asahi Group investigating data leak after ransomware claim
🔹 Oracle E-Business Suite 0-Day (CVE-2025-61882)
Unauthenticated RCE actively exploited in the wild. Oracle released an emergency patch following alerts from Google Mandiant and CISA.
Patch immediately and restrict external access to EBS interfaces.
🔗 Oracle: Security Alert Advisory CVE-2025-61882
🔹 Gladinet CentreStack / Triofox LFI → RCE (CVE-2025-11371)
A Local File Inclusion flaw allows stealing machineKey and forging ViewState to achieve RCE. Actively exploited; no vendor patch yet.
Apply Huntress Web.config mitigation and isolate public interfaces.
🔗 Huntress: CentreStack LFI exploited in the wild
🔹 CISA adds seven CVEs to Known Exploited Vulnerabilities
CISA added seven new entries to its KEV catalog - federal agencies must patch under mandatory deadlines.
Check your asset inventory against the updated list.